Chronometry - a transparent and cryptographically verifiable proof-of-hack signature store

The ever-evolving cybersecurity landscape demands a unified and standardized approach to tackle emerging threats effectively. Hackers and bug bounty hunters play a crucial role in identifying vulnerabilities within systems and applications, helping organizations fortify their defenses against potential threats.
Yokai’s vision for the cybersecurity ecosystem is to create a security collaboration ecosystem engendering better practices and uniting the industry under one common standard. A significant step towards achieving this vision is Chronometry, a cutting-edge tamper-proof platform designed to revolutionize the way hackers record and preserve Proof-of-Hacks (PoH).
The Science of Accurate Time Measurement:
Chronometry takes its name from the science of accurate time measurement. Just as precise timekeeping is essential for various scientific disciplines, maintaining the chronology of Proof-of-Hacks is vital for the cybersecurity community. It provides an immutable record of when a vulnerability was discovered and reported, thereby enhancing transparency and credibility in the hacker community.
Understanding Proof of Hack (PoH):
A “Proof of Hack” refers to compelling evidence or a demonstration that a hacker has successfully exploited a vulnerability in a system or application. This proof is essential to verify the authenticity of a vulnerability report, giving organizations the confidence to address the identified weaknesses promptly.
The Role of Hashes in Hacker Communication:
Hackers often share details of their exploits or vulnerability findings with fellow hackers through various channels, including social media platforms like Twitter. To ensure the integrity of the shared data and to prevent tampering, hackers utilize a cryptographic technique called hashing. A hash is a unique representation of a file, in this case, the Proof-of-Concept or vulnerability report. It acts as a digital fingerprint, making it possible to verify the authenticity and integrity of the data.
Introducing Chronometry.
Chronometry serves as a secure and public ledger for hackers and bug bounty hunters to document their Proof-of-Hacks. Chronometry combines several different technologies that focus on cryptographically verifiable transparency logs and timestamping services. Chronometry can be used independently as one single process, and together with other bug bounty or vulnerability disclosure procedures.
By generating cryptographically signed signatures of the report before submitting it to bug bounty platforms, hackers can create an immutable public fingerprint of the findings. These fingerprints are signed by Chronometry and recorded as entries as part of the Merkle tree becoming part of the Merkle leaf hash computation. Thus ensuring that the data remains unaltered and tamper-evident, providing authentic and time-stamped records of the discovery. Chronometry relies on the ED25519 curve for the signature generation.
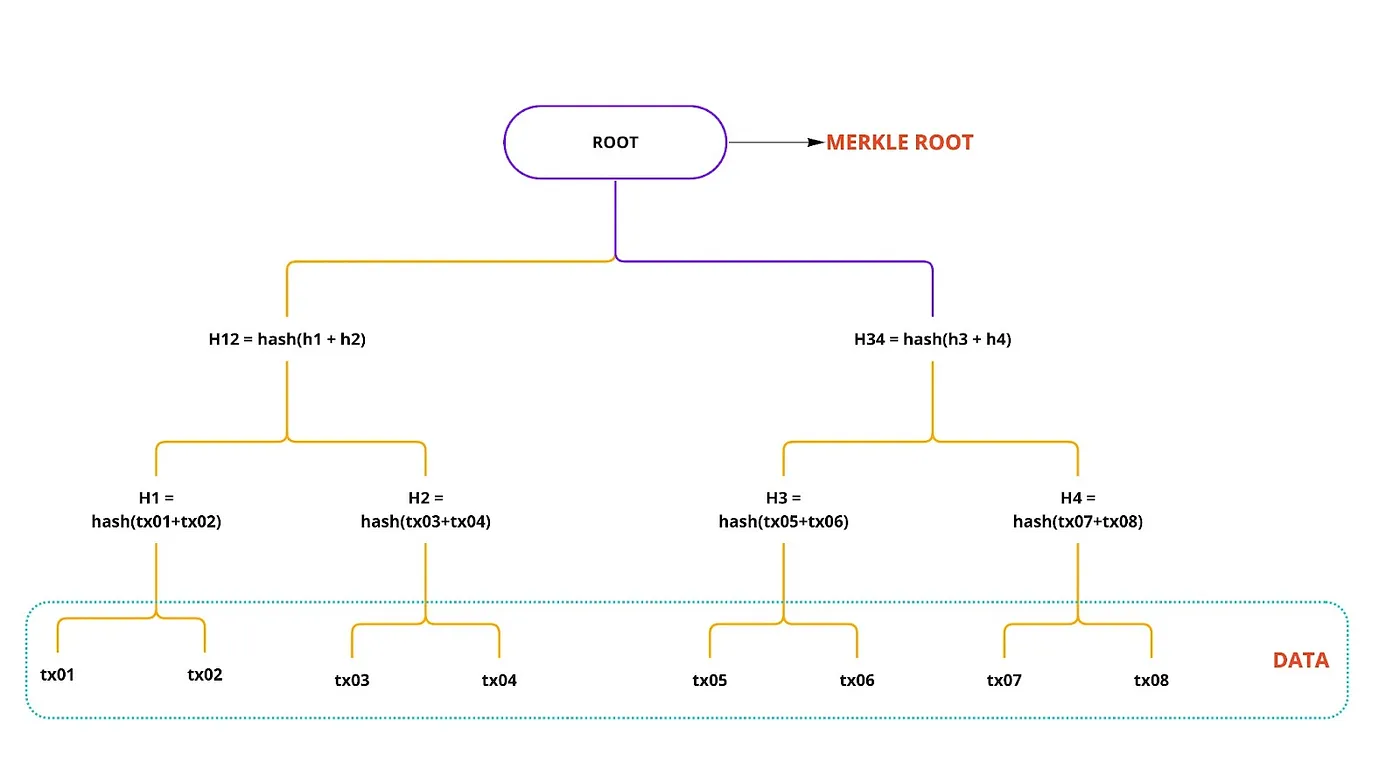
How Chronometry helps:
Immutable Proof-of-Hacks: Through cryptographic hashing, Chronometry creates unique and unalterable fingerprints of vulnerability reports with an IPFS backup. This ensures that the data’s authenticity and chronological order remain intact, serving as the basis for standardization.
Verifiable Time Stamps: The science of accurate time measurement within Chronometry allows for verifiable time stamps on each PoH entry. This feature empowers the cybersecurity community to resolve disputes and determine the first discoverer of a vulnerability accurately.
Dispute Resolution: In cases where multiple parties claim to have reported the same vulnerability, Chronometry’s verifiable timestamps can be used to resolve disputes effectively.
Improved Collaboration: Hackers can securely share their findings with others, confident that the data’s integrity remains intact, leading to increased collaboration and knowledge sharing.
Benchmark for Industry Practices: Yokai’s Chronometry sets a benchmark for industry standards, encouraging the other players to adopt standardized practices. This creates a cohesive approach across the industry, making it more robust against cyber threats.
How to use Chronometry:
Instructions for installation, usage, and verification are available in the repository where the code for Chronometry is published.
Installation
❯ brew tap ant4g0nist/tap
❯ brew install cmetryUpgrading
❯ brew update && brew upgrade ant4g0nist/tap/cmetryKey Generation
Generate a new Chronometry key pair:
# Keys will be saved in ~/.chronometry/
❯ cmetry keys generate
# Keys will be saved in ~/mykeys/
❯ cmetry keys generate --output ~/mykeys/
# Keys will be saved in ~/mykeys/ with the name mykeys
❯ cmetry keys generate --output ~/mykeys/ --name mykeys
# Keys and encrypt them with a passphrase
❯ CHRONOMETRY_PASSWORD=myPassPhrase cmetry keys generate --output ~/mykeys/ --name mykeys
# Keys and encrypt them with a passphrase
❯ cmetry keys generate --output ~/mykeys/ --name mykeys --passphrase mypassphrase
# Keys non-interactively
❯ cmetry keys generate --output ~/mykeys/ --name mykeys --passphrase mypassphrase --yesReport
Chronometry uses yaml format specified below to create a report.
version: 102
author:
name: John Doee
email: john@doe.io
url: https://yokai.network/hacker/john-doe
platform: Yokai
title: Sample Vulnerability Report in function X
description:
This is a sample vulnerability report in function X. It is intended to demonstrate the
capabilities of the vulnerability report format.
This is a multi-line description. It is intended to demonstrate the
capabilities of the vulnerability report format.
severity: Critical
# extra attributes
attributes:
- name: Attribute 1
value:
This is a multi-line attribute value. It is intended to demonstrate the
capabilities of the vulnerability report format.
- name: Attribute 2
value: Value 2
attachments:
- name: Sample Attachment 1
# path can be a local PoC file
path: ./examples/sample.zip
- name: Sample Attachment 2
# # path can be a local PoC file
path: ./examples/file_example_MP4_480_1_5MG.mp4The above report format is used by Chronometry client to create a signature that can be used to verify the authenticity of the report. The report is signed using the private key of the user. The signature is then used to generate a PoH of the report. The PoH is then recorded on the Trillian Log.
Generate a PoH
❯ cmetry sign -h
Sign the supplied Vulnerability Report. This command will generate a signed blob that can be posted to the Chronometry's public data store.
Usage:
cmetry sign [flags]
Flags:
-b, --blob string write the blob to FILE
-h, --help help for sign
--input string The folder to search the public and private key files. (default "~/.chronometry")
--name string The base name for the public and private key files. The public key file will have the suffix '.pub' appended to the name. (default "id_ed25519")
-o, --output-signature string write the signature to FILE
--passphrase string The passphrase to decrypt the private key.
-f, --reportFile string A vulnerability report file to calculate generate the signature for.
-a, --show-author Show the author's name in the report. By default, the author's name is hashed and included in the signatureIf you have a report file examples/sample-report.yaml you can generate a PoH using the following command:
❯ cmetry sign -f examples/sample-report.yaml --passphrase password -b output.poh -a-a flag is used to include the author's name in the report. By default, the author's name is hidden (so, author name in the PoH records will be Anonymous), only hash of the name is included in the signature.
cat output.json
{
"Report": {
"Version": "N4NPLyV2LyPh90pTHL5EXbc9Z2Xr5gh4p9--zX1K9uE=",
"Title": "HsAB38Ftx9vQ-y_-7RnbAsXgwGpputFo19ZFtEx_yAQ=",
"Description": "CimMqMLdUqYVqHiXtuVe7U0ZfuVxtsltuSVVbS1UVfA=",
"Attributes": "G8acHYAMEp7uwz2eMyOTRuQEQLpCqVUFRvz9zySTSq8=",
"Author": "Anonymous",
"AuthorDetailsHash": "eDMQAUUWZFUUpMjN1Ujb_Fjw6BDFNM0fRJ1HxFPX-v4=",
"Platform": "fDIzedm5COBGBl4mq24iXixHI8OO9j2gEKel34SyPKs=",
"Severity": "Qn3SlpvRQL7DwbzHmD2pgvSBWTjNRRCtCyutSKxbVfk=",
"Attachments": "IqamhAdadrzbur3x_7GOYVrwHn6xFeCz1E1MjwqJ8m0="
},
"PublicKey": "Hp2mvMiSc1XFhBUGxaQc0br/CtJrNBkiMTUoORCzRP4=",
"Signature": "JMFwICkm2mtVLhAYFi5LaCvfnQt8XY7LwonkNgx08jCX3kMjGg6iJoeATyGFelyN0z2X4BxEyq1N9ojaNimVAg=="
}Verify a PoH
You can verify a PoH using the following command:
❯ cmetry verify -r output.poh
⌛️Verifying signature...
publicKey: Hp2mvMiSc1XFhBUGxaQc0br/CtJrNBkiMTUoORCzRP4=
signature: JMFwICkm2mtVLhAYFi5LaCvfnQt8XY7LwonkNgx08jCX3kMjGg6iJoeATyGFelyN0z2X4BxEyq1N9ojaNimVAg==
✅Signature verification successfulYou can also verify a PoH record on the Chronometry's Trillian Log Server using the following command:
❯ cmetry verify -i 12 -s http://localhost:8008
publicKey: Hp2mvMiSc1XFhBUGxaQc0br/CtJrNBkiMTUoORCzRP4=
signature: sWKfA4/aD1hV0h36QpBEeIh5MTAM8IHPFNND2WFbz3m+3z60Ls6Srh6DkHIyyvQzgW7WjS8M/fpU/Fyprcu3Dw==
⌛️Verifying signature...
✅Signature verification successfulRecord a PoH
To record the generated PoH on the Chronometry's Trillian Log Server, you can run a command similar to the following:
❯ cmetry record -f output.json -s http://localhost:8008
ETag: 29912308828015d2920df6861b0dbda4080aad6e4e5e91f75433969e31161c07
Location: chronometry.io/?uuid=29912308828015d2920df6861b0dbda4080aad6e4e5e91f75433969e31161c07
Payload:
Key: 7a19e0d4eaed06f829912308828015d2920df6861b0dbda4080aad6e4e5e91f75433969e31161c07
IntegratedTime: 1690202999
LogID: 7a19e0d4eaed06f8
LogIndex: 101
Verification:
InclusionProof:
Checkpoint: bG9jYWxob3N0IC0gODc5ODMxMDU1MjEyNDA2NTUyOAoxMDIKM0dueGd5dFJaVU9oNTNZWDREQ2RpM1ZBc2tTbVB0K045UEZDOStlOVk2OD0KVGltZXN0YW1wOiAxNjkwMjAyOTk5NzQ2Njc1MDAwCgrigJQgbG9jYWxob3N0IFBLNmJZY2dkQUNiOE1RZis3aStQUkRYdFdJZTFvaHZtRlF2enFhMURYYk02dVFvY3RndTdMTVVNd0ZGOHFSd3ROdlhLdEFSajBaZlRGRFZZUXJZS0pBUFRod1E9Cg==
Hashes: [f7f2756ddaa8b2a8dce8d74be128d9e11a05a9d202090cd9e24a12cca1b56ecb 297c6f09de2dfed365a627dc336d376f9fe070c76b02f61911d2d6c2e4d659a5 0d0b2be6e839f3c0d1ca14536f67f899d3ceab56c720fbb0f9dec9cd4bd3fe27 c1f81d2881d8f11caaf4080abf8941bda11015be838ceb0189eb44fceffde178]
LogIndex: 101
RootHash: dc69f1832b516543a1e77617e0309d8b7540b244a63edf8df4f142f7e7bd63af
TreeSize: 102
SignedEntryTimestamp: OS3bTQYxWzSFic/VL2WcJ0wOQ4ky+2kVg9DAKTszrAu4rUnr9xL4u60CCXhpbSVPnf2YwPCMKMSLuCEXM/jiCQ==
Report uploaded successfully
Happy Hacking 🎉